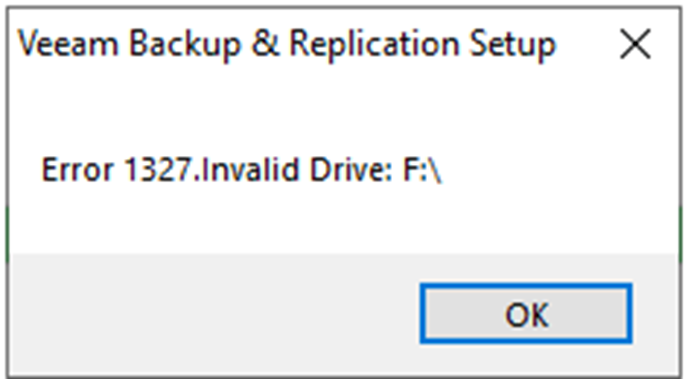
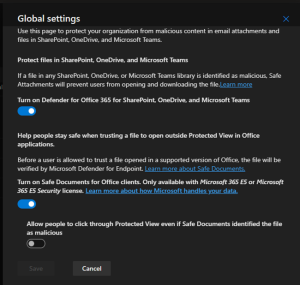
If it happened Error 1327.Invalid Drive when you tried to upgrade Veeam Bavkup &...
Month: March 2022
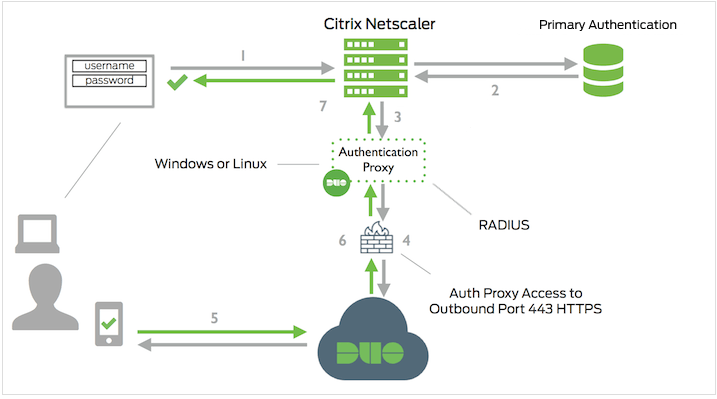
To add Duo two-factor authentication to your Citrix Gateway with nFactor you'll configure the...
Veeam released patches for Veeam Backup & Replication on March 12, 2022. Multiple vulnerabilities...