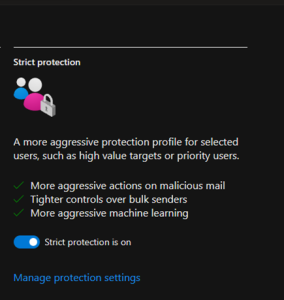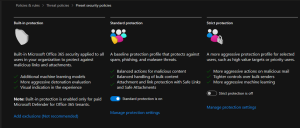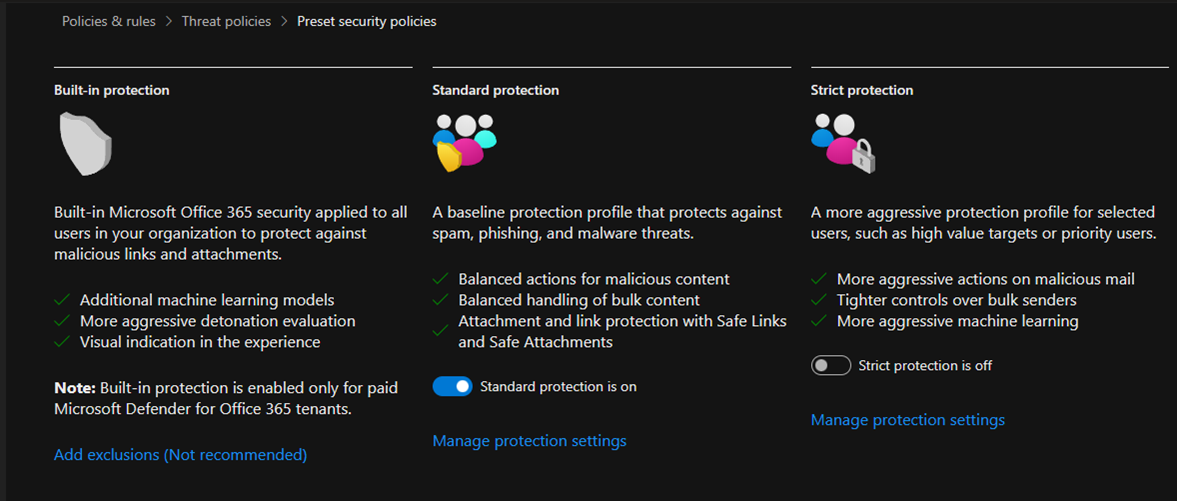
Microsoft Defender for Office 365 provides preset security policies to help organizations protect their Office 365 environment from various threats. These preset policies are designed to offer baseline protection and can be customized according to the organization’s specific requirements.
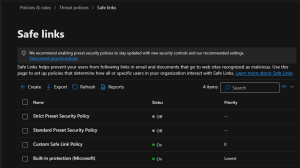
Preset security policies are predefined rules and configurations designed to establish a baseline level of security within an organization’s IT infrastructure. These policies are foundational guidelines for implementing security controls and protecting against common threats.:
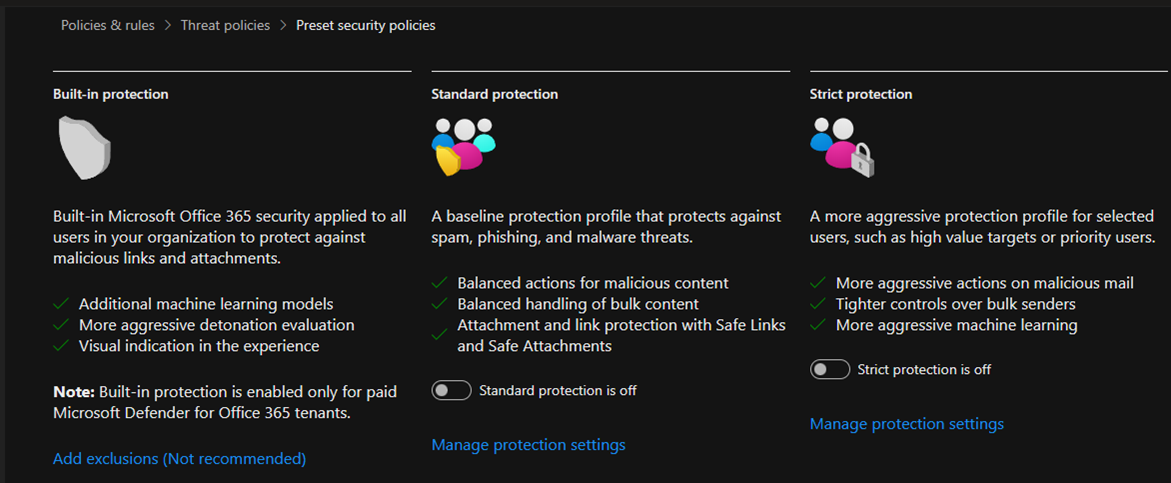
- Standard protection
- Strict protection
- Built-in protection
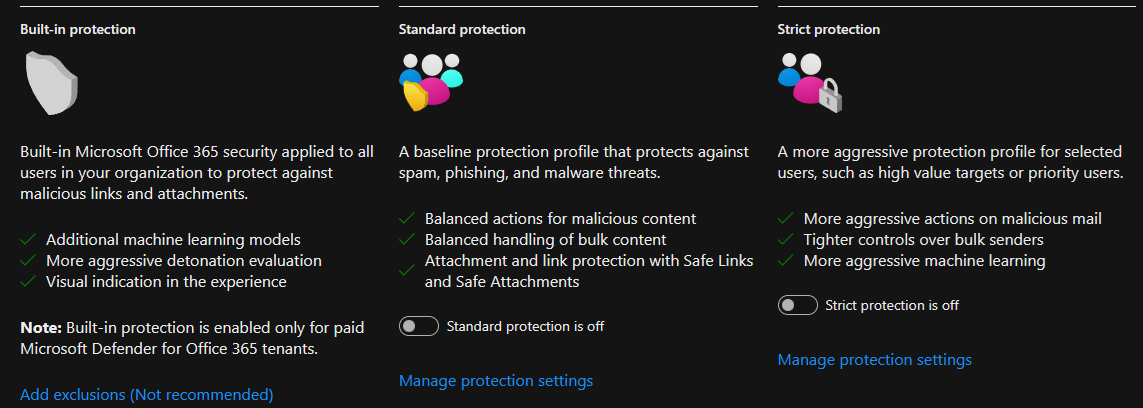
To assign Standard preset security policies to users using the Microsoft Defender Security Center portal, you can follow these general steps:
1.Login to the Microsoft Defender portal using your organization’s credentials.
https://security.microsoft.com/
2.Expand the Email & collaboration on the Microsoft Defender page and select Policies & rules.
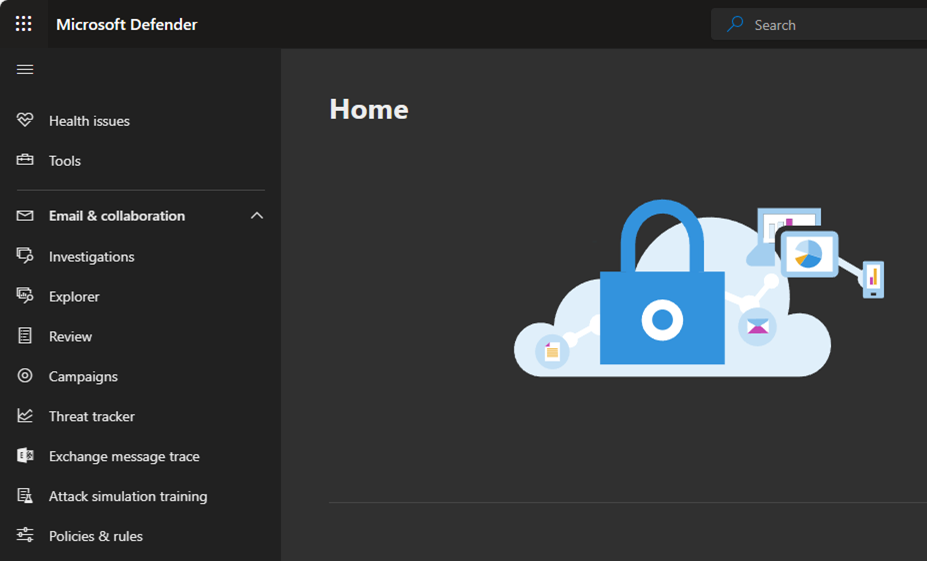
3.Select Threat policies on the Policies & rules page.
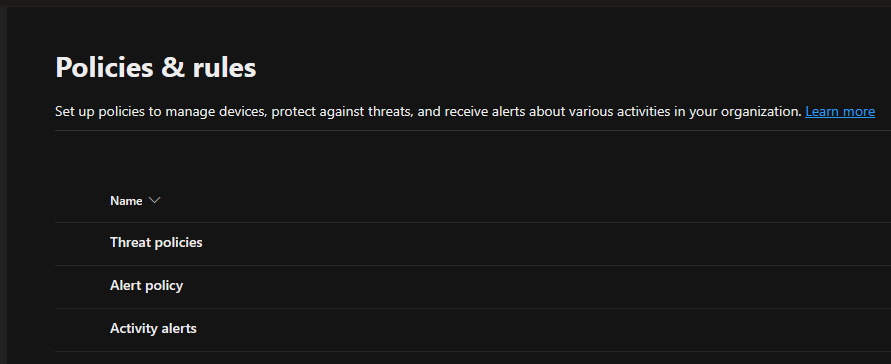
4.Select Preset Security Policies on the Threat policies.
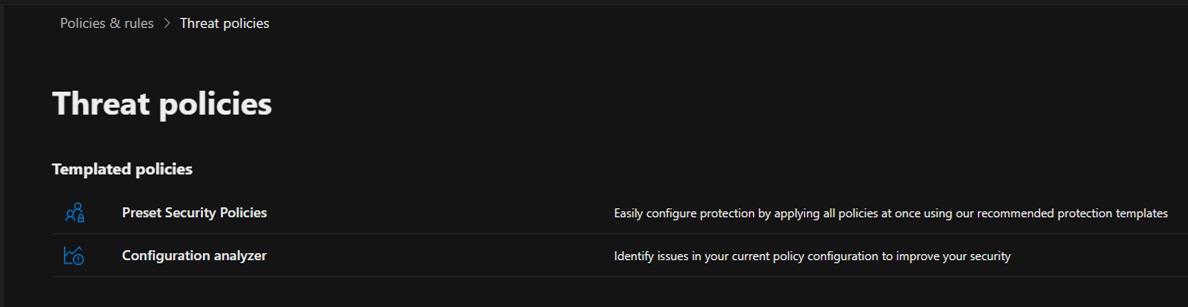
5.On the Preset security policies age, click Manage protection settings of Standard protection.
6. On the Apply Exchange Online Protection page, select All recipients and click Next. You can also select the Exclude these recipients option and configure the recipient exceptions.

7. Select All recipients on the Apply Defender for Office 365 Protection page and click Next. You can also select the Exclude these recipients option and configure the recipient exceptions.
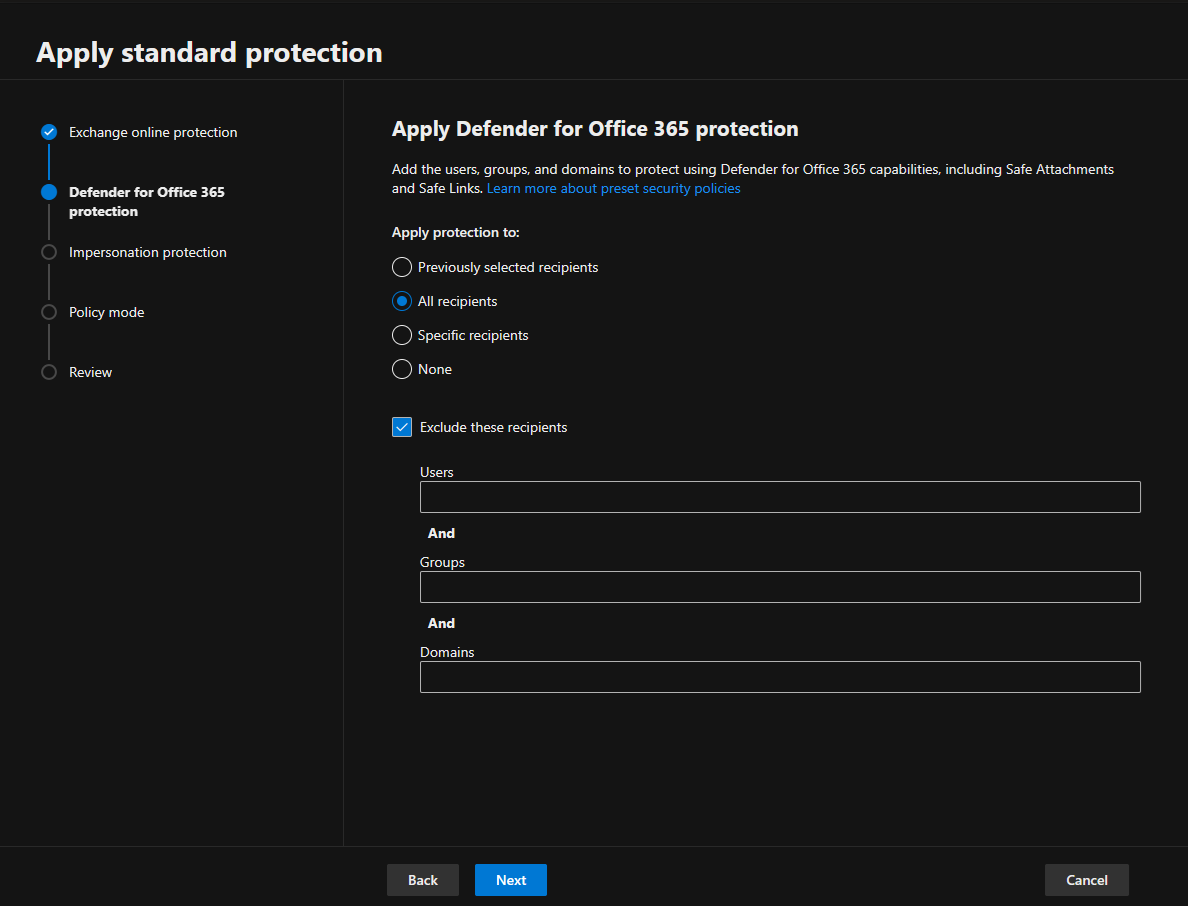
8.Click Next on the Impersonation protection page and define protect against impersonation techniques.
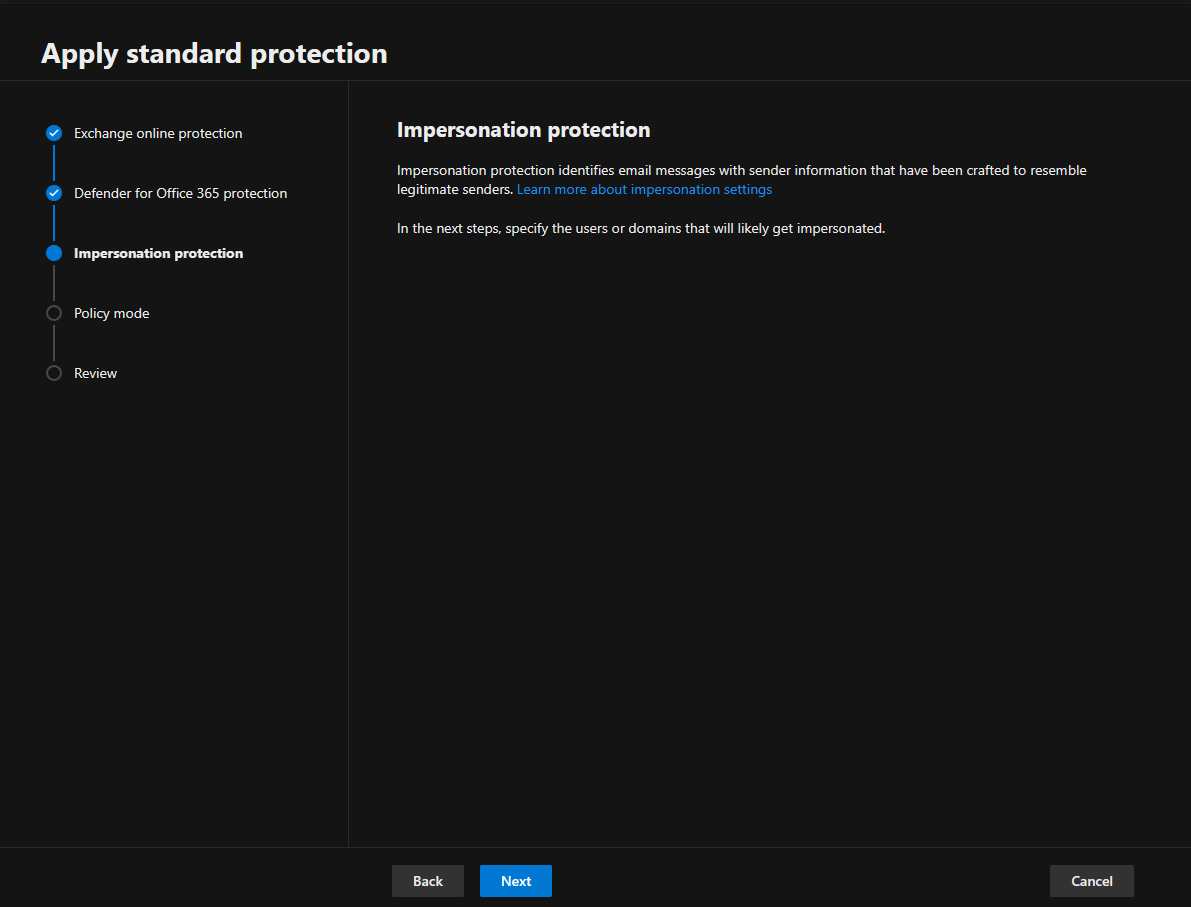
9.On the Add email addresses to flag when impersonated by attackers page, add internal and external senders protected by user impersonation protection and click Next.
Note:
In the Standard or Strict preset security policy, you can specify a maximum of 350 users for user impersonation protection.
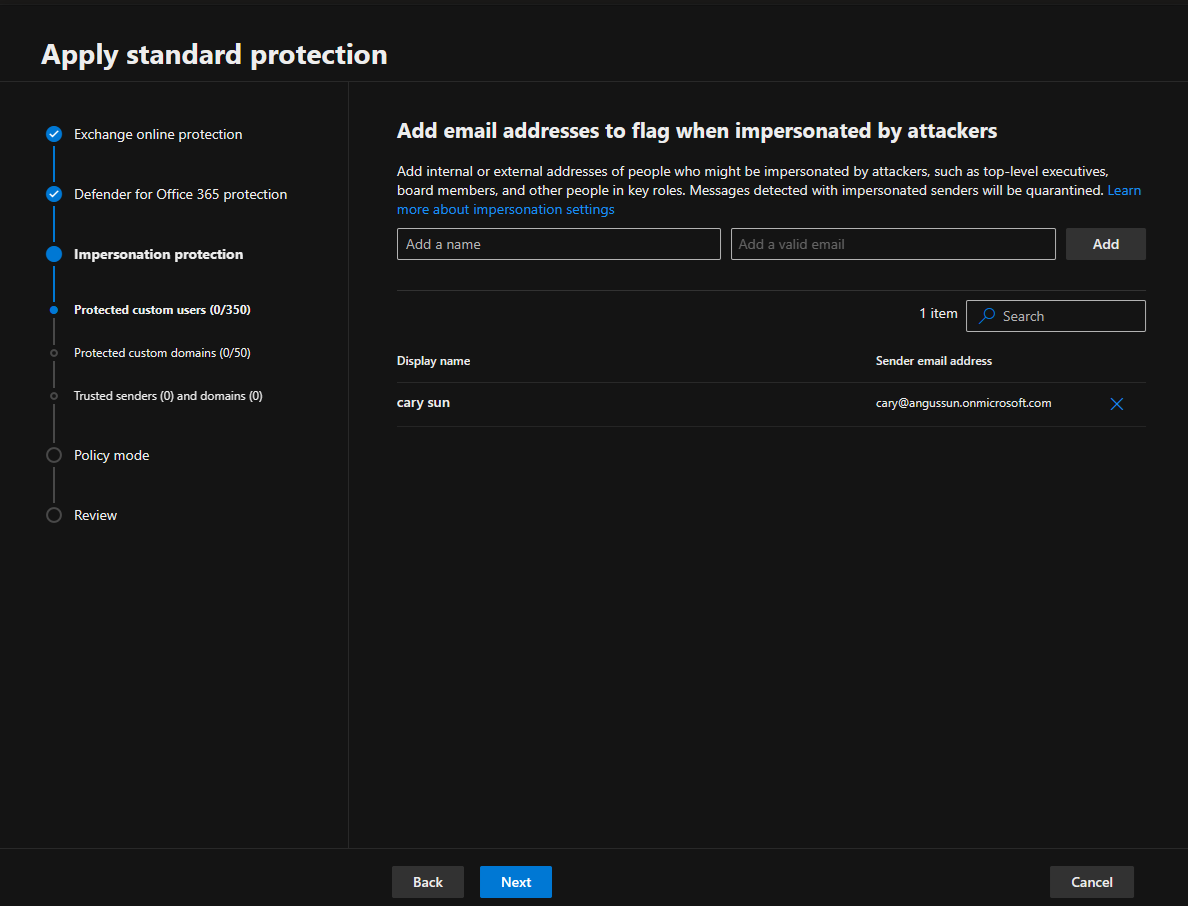
10.On the Add domains to flag when impersonated by attackers page, add internal and external domains protected by domain impersonation protection and click Next.
Note:
In the Standard or Strict preset security policy, you can specify a maximum of 50 custom domains for domain impersonation protection.
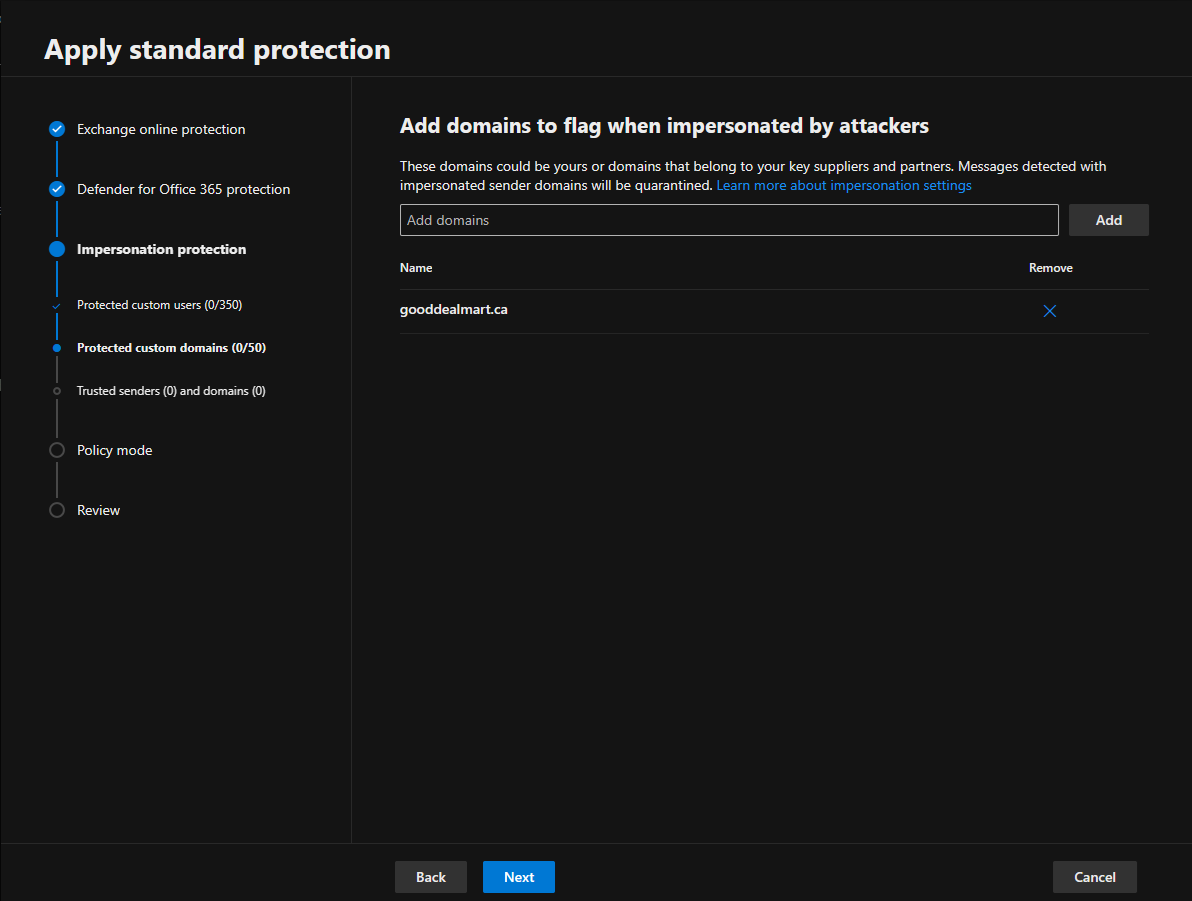
11. On the Add trusted email addresses and domains to not flag as impersonation page, enter the sender email addresses and domains you want to exclude from impersonation protection and click Next. To ensure that emails from trusted sources are not mistakenly flagged as impersonation attempts in Microsoft Defender for Office 365, you can add these trusted email addresses and domains to the Safe Senders and Safe Domains lists.
Note:
Trusted domain entries don’t include subdomains of the specified domain. You need to add an entry for each subdomain.
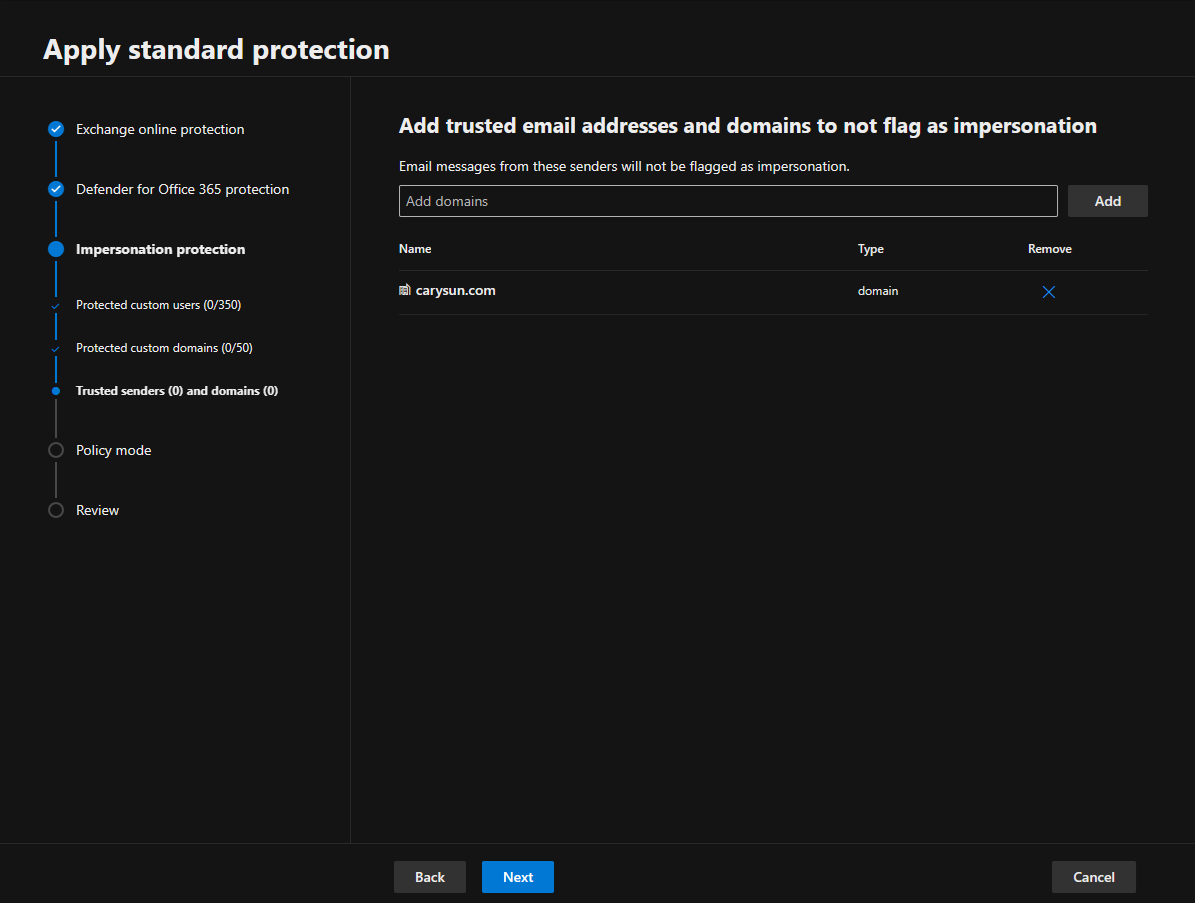
12.Select Turn on the policy when finished on the Policy mode page and click Next.
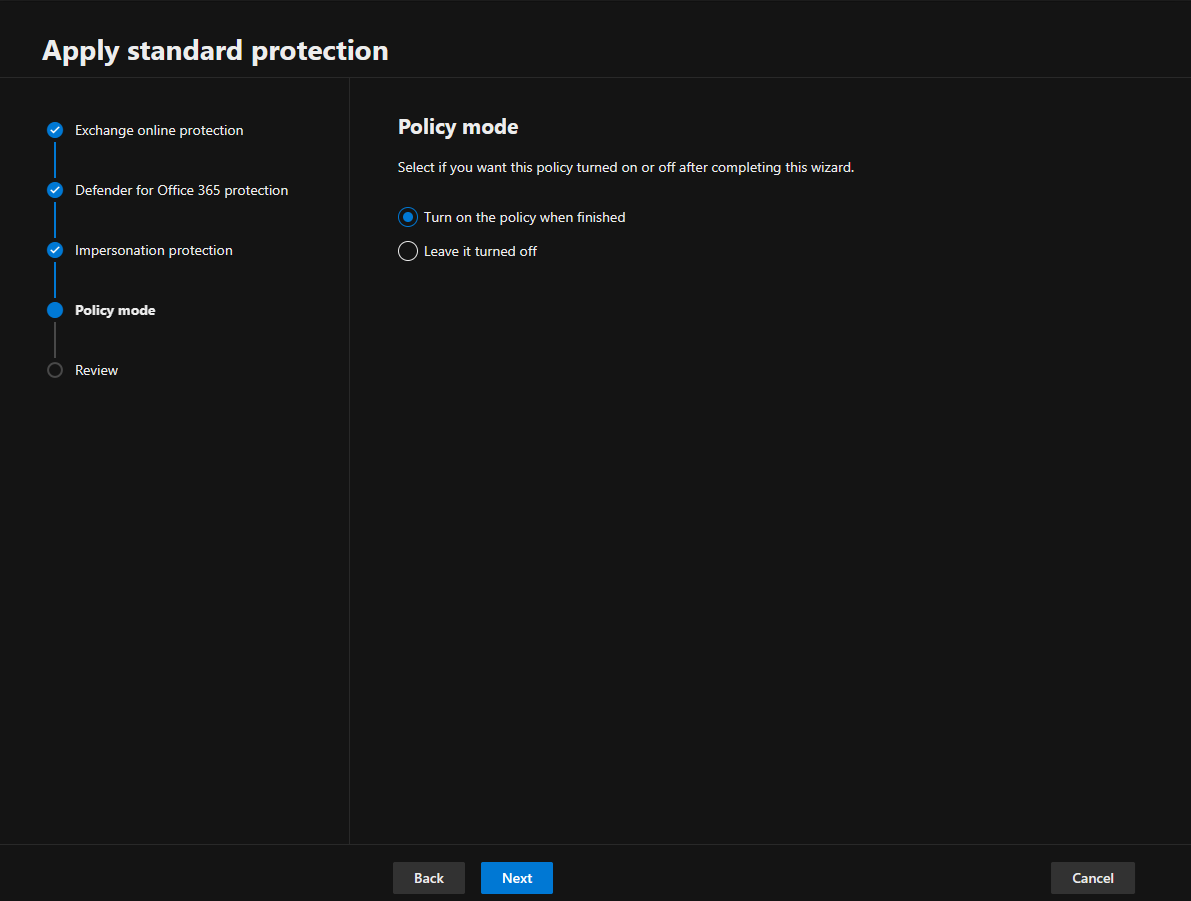
13.Click Confirm on the Review page.
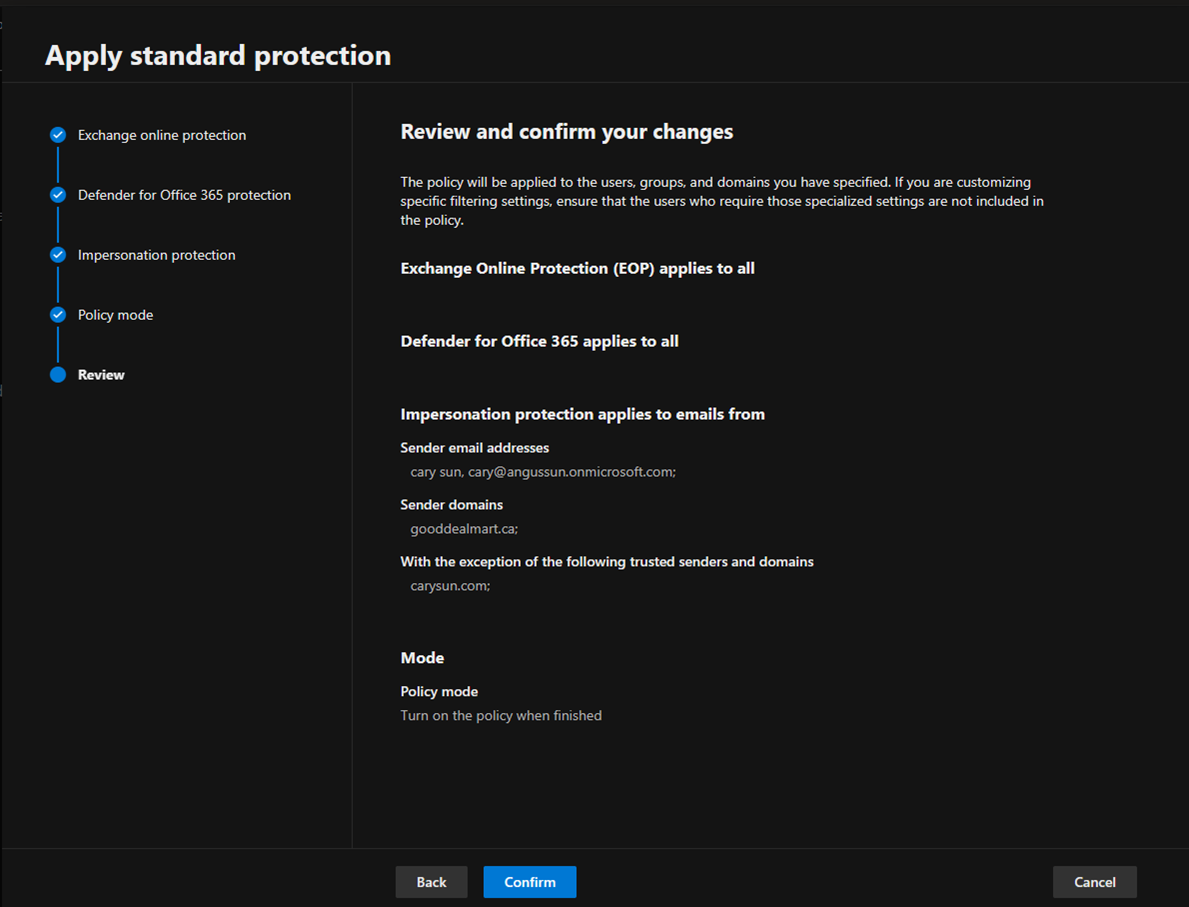
14.Ensure Standard protection updated and click Done.
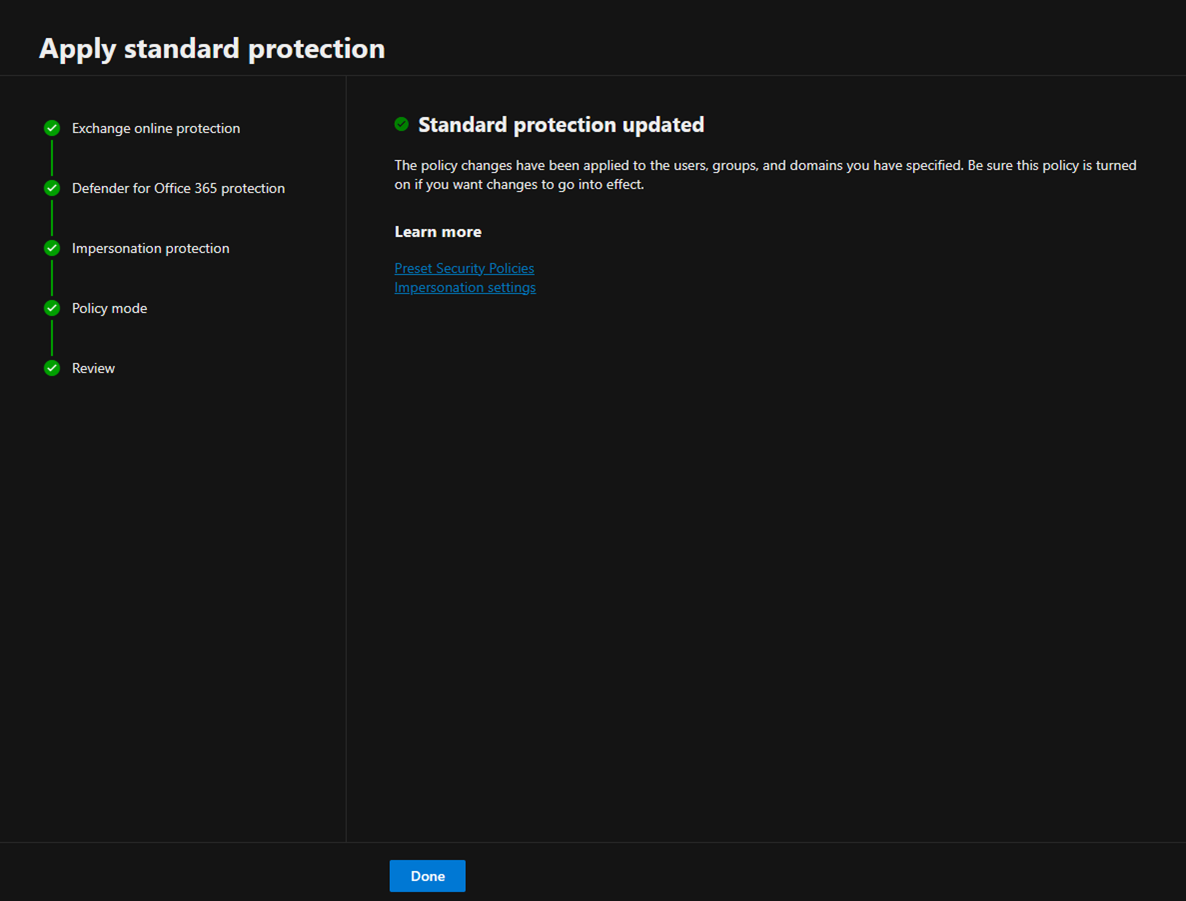
15.Ensure Standard protection is on.

I hope you enjoy this post.
Cary Sun
X: @SifuSun
Web Site: carysun.com
Blog Site: checkyourlogs.net
Blog Site: gooddealmart.com
Amazon Author: Amazon.com/author/carysun
Author: Cary Sun
Cary Sun has a wealth of knowledge and expertise in data center and deployment solutions. As a Principal Consultant, he likely works closely with clients to help them design, implement, and manage their data center infrastructure and deployment strategies.
With his background in data center solutions, Cary Sun may have experience in server and storage virtualization, network design and optimization, backup and disaster recovery planning, and security and compliance management. He holds CISCO CERTIFIED INTERNETWORK EXPERT (CCIE No.4531) from 1999. Cary is also a Microsoft Most Valuable Professional (MVP), Microsoft Azure MVP, Veeam Vanguard and Cisco Champion. He is a published author with several titles, including blogs on Checkyourlogs.net, and the author of many books.
Cary is a very active blogger at checkyourlogs.net and is permanently available online for questions from the community. His passion for technology is contagious, improving everyone around him at what they do.
Blog site: https://www.checkyourlogs.net
Web site: https://carysun.com
Blog site: https://gooddealmart.com
Twitter: @SifuSun
in: https://www.linkedin.com/in/sifusun/
Amazon Author: https://Amazon.com/author/carysun