Authenticated Received Chain (ARC) is a mechanism used in email authentication protocols to address the issues of message forwarding and intermediary handling of emails. It is designed to improve the reliability and security of email authentication systems like SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail).
When an email is forwarded or relayed through multiple mail servers, the sender’s original authentication information may become unreliable or lost entirely. This can lead to problems such as SPF or DKIM signature verification failures, flagging legitimate emails as spam or phishing attempts.
ARC aims to solve these problems by creating a cryptographic chain of custody for an email message as it passes through intermediate mail servers. This chain allows each server in the delivery path to add its authentication information to the email header without breaking the original SPF or DKIM signatures.
Authenticated Received Chain (ARC) consists of three main components:
ARC-Seal: The ARC-Seal is a cryptographic signature added by each intermediate mail server in the email delivery chain. It includes information about the actions taken by the server, such as forwarding or relaying the message, as well as the results of any authentication checks performed by the server. The ARC-Seal helps establish the authenticity and integrity of the email delivery chain.
ARC-Message-Signature (AMS): The ARC-Message-Signature is added by the originating email server and covers the entire message, including the email headers and body. It serves as the initial cryptographic signature for the email and is used to verify the integrity of the message content. The AMS signature is carried through the entire delivery chain and is augmented by ARC-Seals added by intermediate servers.
ARC-Authentication-Results (AAR): The ARC-Authentication-Results header aggregates the authentication results from all intermediate servers in the email delivery chain. It summarizes the authentication checks performed by each server, including SPF, DKIM, and DMARC (Domain-based Message Authentication, Reporting, and Conformance) results. The AAR header helps the final destination server assess the trustworthiness of the email based on the collective authentication status of all servers involved in the delivery process.
Trusted ARC sealers are email services that provide valid and trustworthy Authenticated Received Chain (ARC) signatures to preserve the original email authentication information. You might need to use trusted ARC sealers when you have legitimate intermediate services that modify the messages before they are delivered to your Microsoft 365 organization, which can cause email authentication failures such as SPF, DKIM, or DMARC.
Before adding Trusted ARC sealers in the Microsoft Defender for Office 365, you must be assigned permissions as one of the below.
-Microsoft Defender XDR Unified role-based access control (RBAC) (Affects the Defender portal only, not PowerShell): Authorization and settings/Security settings/Core Security settings (manage) or Authorization and settings/Security settings/Core Security settings (read)
-Exchange Online permissions: Membership in the Organization Management or Security Administrator role groups.
-Microsoft Entra permissions: Membership in the Global Administrator or Security Administrator roles gives users the required permissions and permissions for other features in Microsoft 365.
Configure trusted ARC sealers
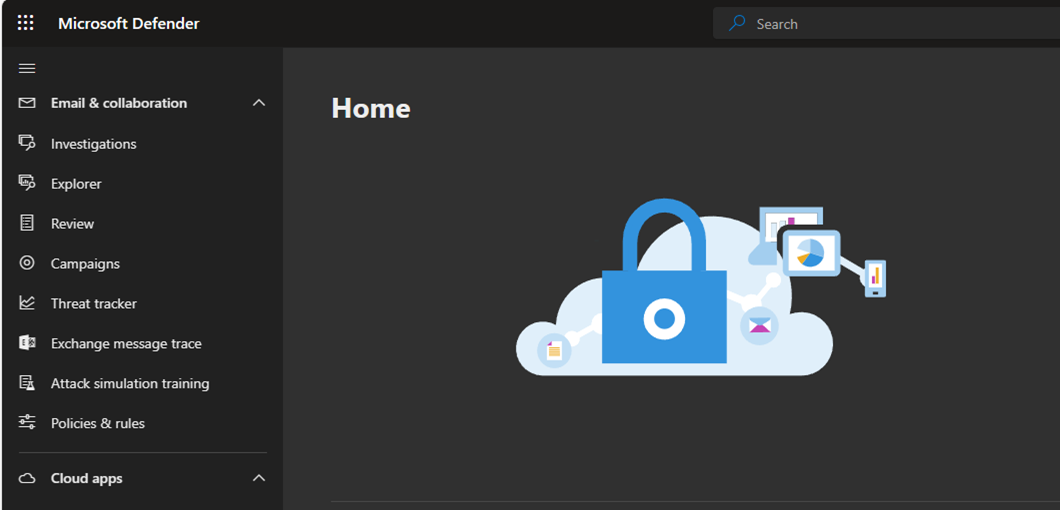
1.Login to the Microsoft Defender portal, expand Email & collaboration and select Policies & rules.
https://security.microsoft.com/

2.Select Threat policies on the Policies & rules.
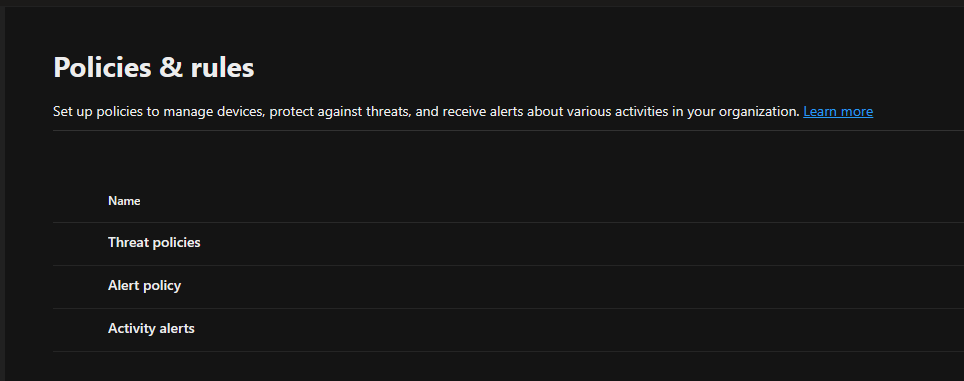
3,Select Email authentication settings in the Rules session.
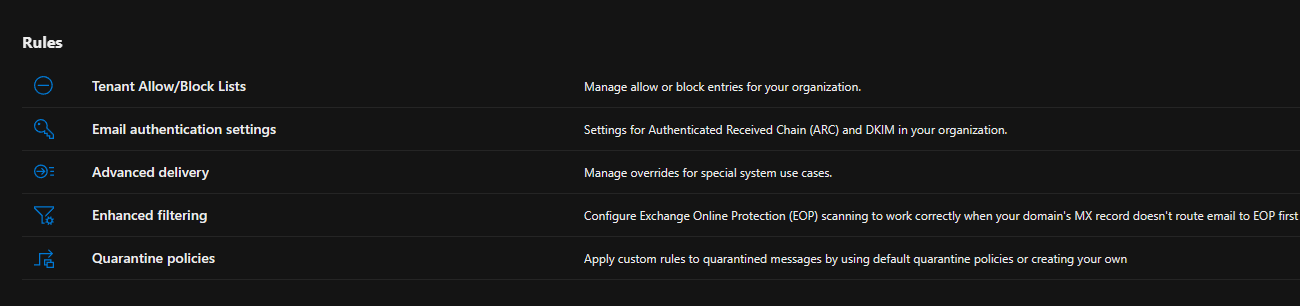
4.On the Email authentication settings page, select ARC tab and click Add,
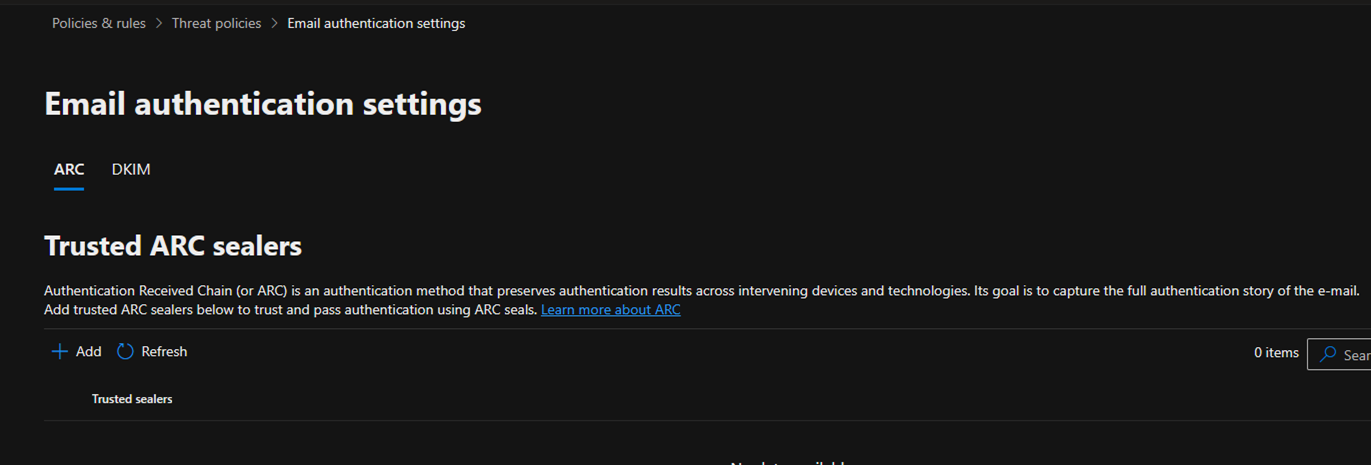
5.Enter the trusted signing domain and click Save.
Note:
The domain name must match the domain shown in the d value in the ARC-Seal and ARC-Message-Signature headers in affected messages.
6.Click Yes to complete this task.
I hope you enjoy this post.
Cary Sun
X: @SifuSun
Web Site: carysun.com
Blog Site: checkyourlogs.net
Blog Site: gooddealmart.com
Amazon Author: Amazon.com/author/carysun
Author: Cary Sun
Cary Sun has a wealth of knowledge and expertise in data center and deployment solutions. As a Principal Consultant, he likely works closely with clients to help them design, implement, and manage their data center infrastructure and deployment strategies.
With his background in data center solutions, Cary Sun may have experience in server and storage virtualization, network design and optimization, backup and disaster recovery planning, and security and compliance management. He holds CISCO CERTIFIED INTERNETWORK EXPERT (CCIE No.4531) from 1999. Cary is also a Microsoft Most Valuable Professional (MVP), Microsoft Azure MVP, Veeam Vanguard and Cisco Champion. He is a published author with several titles, including blogs on Checkyourlogs.net, and the author of many books.
Cary is a very active blogger at checkyourlogs.net and is permanently available online for questions from the community. His passion for technology is contagious, improving everyone around him at what they do.
Blog site: https://www.checkyourlogs.net
Web site: https://carysun.com
Blog site: https://gooddealmart.com
Twitter: @SifuSun
in: https://www.linkedin.com/in/sifusun/
Amazon Author: https://Amazon.com/author/carysun